Charlie Miller’s and Chris Valasek’s talk at Defcon 23 last year detailed the surprisingly long list of things hackers can do to a connected vehicle. Before this, many consumers couldn’t have imagined their air conditioning and entertainment systems shutting off in response to a hacker’s unauthorized input.
Miller and Valasek were able to make a Jeep stop dead on the highway, and even more surprising, they did it remotely. As recently as 2013, when the security researchers were in the backseat of a Ford Escape, they needed to connect to the OBD2 port for similar hacks.
Constant Vulnerability
Fast forward to 2016 and we see the white-hat hacks continue. In fact, Miller and Valasek recently described how new attacks could affect future car owners, some of which, could even be fatal for drivers. Tencent, a telecom giant based in China, recently uncovered the now-corrected flaws that allowed them to take control of a Tesla Model S. It was reported to the manufacturer, but what if future discoveries like this fall into the wrong hands?
For connected car manufacturers, there are many aspects of a breach to consider, and learning the optimal way to defend against hackers will be an ongoing issue. When learning about a hack, car manufacturers essentially have two choices: fix the flaw, or fix the chain of security vulnerabilities that led to the overall compromise. Some automakers like Tesla are doing the latter, working with hackers, testers, and researchers to create software updates shortly after the issue.
Beyond Infotainment
As infotainment systems merge with the Internet-of-Things and expand their device connectivity, more automotive companies will have to work with original equipment manufacturers to improve not just infotainment operating systems’ features and connectivity, but the security precautions that go into developing them.
This extensive process pales in comparison to how easy it might actually be for hackers to get into your car.
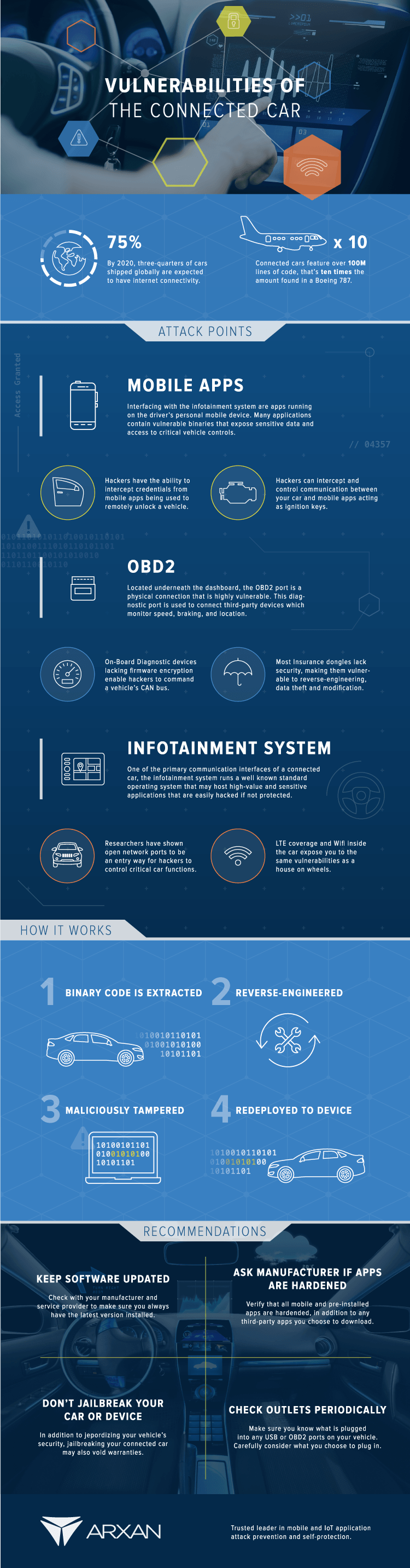
According to Arxan Technologies’ page on automotive IoT, hackers would be interested in lifting cryptographic keys used by a car’s electronic systems, including the OBD2 port found under every post-1995 vehicle’s dashboard. Shown as the second attack point on their graphic, the on-board diagnostics systems in some cars lack firmware encryption, which means that hackers could extract the binary code of that system with a scanner quite easily.
Future Considerations
As self-driving cars enter the picture, the thought of a hacker accessing your car is even more scary. What happens if someone maliciously takes control of your vehicle remotely – or an entire expressway full of autonomous vehicles? The implications and ramifications of this are almost beyond measure. The infographic below from Arxan Technologies highlights the attack points of the average connected car and how to defend against them.